Jules : Mmm-mmmm. That is a tasty burger. Vincent, ever have a Big Kahuna Burger? [Vincent shakes his head] Jules : Wanna bite? They’re real tasty. Vincent : Ain’t hungry. Jules : Well, if you like burgers give ’em a try sometime. I can’t usually get ’em myself because my girlfriend’s a vegitarian which pretty much makes me a vegitarian. But I do love the taste of a good burger. Mm-mm-mm. You know what they call a Quarter Pounder with cheese in France? Samuel L Jackson as Jules and John Travolta as Vincent |
Pulp Fiction (1994) directed by Quentin Tarantino
This article is not about Pulp Fiction. But I must say, Quentin Tarantino, what a genius! What a mastermind! This movie is one of my personal favorites. If you have not seen the movie, this is a must-see!
What we can take away from this dialogue between Jules and Vincent, and what is also observed in the movie, is that Jules has a good appetite for burgers.
And this article will be focused on appetite. More specifically Risk Appetite as a concept together with Risk Tolerance, and Risk Capacity.
I have, throughout my career, observed that these three different terms Risk Capacity, Risk Tolerance, and Risk Appetite often to be confusing and blurry for risk practitioners, experts, and specialists. This is understandable but this should not be the case I think. But as the terms are rarely discussed or explained, or used verbally more than through fluffy statements or oneliners this definitely contributes to the blurriness. The same goes for the practical application when it comes to risk in general but also explicitly for security risk. More on this later.
And I have also witnessed that here and there the terms can be named differently. And it is very rare to hear these terms to be used in a dialogue when risk is discussed. This sentence is not that common to be said:
“Our capacity related to this risk is 3 on a scale between 1 to 5 and our tolerance is 2.7. This is within our risk appetite which is quantified to be between 2.82”.
This is not how a dialogue takes place when these terms are spoken about…not at least according to my own experience. It is quite rare to hear an organization or persons speak about risk and to be able to articulate, qualitatively or quantitatively, what their risk capacity, risk tolerance, and risk appetite are.
A formulated Risk Appetite statement would though be the instrument to verbally manifest an organization’s risk appetite. But this is not always the case either, that an organization has a formulated risk appetite statement that is sanctioned and developed by the board, and executive leaders, and applied throughout the organization. Or that such a statement is something that finds a way out into the places in an organization where the risks are actually realized. I.e. there is often a disconnection, somewhere along that “statement” into the practical application of it where it can be used in reality to guide individuals and teams in an organization to take the right amount/level of risk.
Risk Capacity, Risk Tolerance, and Risk Appetite are instruments that shall help an organization to make adequate risk decisions, i.e. “take the right amount of risk”.
RISK CAPACITY, TOLERANCE & APPETITE
Before exploring the content of this article, let us put some terms and definitions into context.
Below is a short and simple explanation of each term, that will appear several times in this article:
- Risk Capacity – The maximum amount of Risk an organization is able to take.
- Risk Tolerance – The acceptable amount of deviation of Risk that an organization is able or willing to take from their risk appetite.
- Risk Appetite – The amount of Risk that an organization is willing to take.
To illustrate the relationships between the terms I created a simple model to visualize it as a “range”. Both in theory and practice, I think Risk Appetite, Tolerance, and Capacity are about ranges.
And they are not absolute or static. They may be static for a period of time, but they change. And why is that? This is because Risk is dynamic in itself. And when it comes to a security risk, one of the components that highly contributes to the dynamic characteristics are the “threats”. Security threats can not be predicted, it is impossible. We can though forecast them to a certain extent. If you want to know more about how to forecast the future, take a look at this article EMERGING RISKS & HOW TO FORECAST THE FUTURE.
Risk Appetite, Tolerance, and Capacity are those concepts that easily fall into the limbo land of theoretical concepts that less often find their way into reality. This is my attempt to shine some light on the concepts and hopefully clear out some of the blur and fluffiness.
Risk Appetite, Tolerance, and Capacity in this article will be modeled with the help of the following abstraction:

To provide a further understanding of how these three terms interrelate with each other I will put them into an example. The context will be an explanation consisting of three different business processes (A, B, C) in an organization (XYZ).
Before we jump further into this article following key principles apply:
- Risk Capacity will always be higher compared to tolerance and appetite.
- The Risk Tolerance can be either equal or higher in comparison to the appetite. The Risk Tolerance is the acceptable amount of deviation from the Risk Appetite.
- Risk Appetite should, generally and in most scenarios, correlate with an organization’s acceptance of Risk. The Risk Appetite level should not, in any case, exceed the Risk Capacity level.
Summarized: Risk capacity is the total amount of risk an organization is able to take. Risk tolerance is about controlling the amount of risk the organization is taking. Risk appetite is about accepting the amount of risk an organization is taking.
SCENARIO
Organization XYZ has several business processes, hence BP[capital letter]. In this example, we will look into A, B, and C.
Organization XYZ has a global presence and has existed for 100 years. They have a mixture of old legacy systems (information, IT, OT, and infrastructure) in combination with modern technology (IoT, software, cloud services, hybrid technologies etcetera).
As a part of a Risk Assessment exercise, three of the organization’s core business processes have been assessed (A, B, and C as stated above) to understand and identify their respective Risk Capacity, Risk Tolerance, and Risk Appetite.
INFO
- Business process – is for example production, finance, RnD, sales, HR, marketing etcetera.
Business Process A
Organization XYZ has made heavy investments in BP[A] in terms of machines and technologies during its existence (100 years. Very much of Organization XYZ’s intellectual property gathered through the existence of the organization in terms of knowledge and skills is found within BP[A].
One of Organization XYZ’s core products and services is produced within BP[A]. The bottom-line profit and marginal generated from BP[A] is not considered as high in comparison to other Business processes.
The products and services produced in BP[A] have made Organization XYZ recognized as one of the leading organizations in their field and on the market. This product is produced in bulk and makes up the core of the organization. For this reason, one important factor for Organization XYZ is to make sure the “brand” and reputation are protected.

BP[A] includes many legacy systems (IT, OT, and information) that are coupled with the production environment. Interruptions or production damage will cause a significant negative repetitional impact on Organization XYZ and its brand. The organization has due to these reasons taken an active decision to have a low Risk Tolerance and Risk Appetite level within BP[A].
The data and information, related to the products Organization XYZ produced within BP[A], are classified as sensitive and critical to the organization.
The typical customers for BP[A] are customers who want to make investments in well-tested products and services that have been developed over the years.
Business Process B
Ok so let’s take a look at BP[B] which has been operational for approximately 3 years. Within BP[B] at Organization XYZ is maximizing its Risk Appetite and Risk Tolerance.
BP[B] is highly concentrated on software and digital development. The products and services produced within BP[B] do not have any dependencies on other systems (IT, OT, or information) operating in other Business Processes within Organization XYZ.
The environment within BP[B], where the production of the products and services takes place, has been built up and designed so that data and information are segregated and separated from other entities, units, and processes within Organization XYZ.
The environment is based on modern and new technology, i.e. there is no inheritance bound to a technological, operational, or organizational legacy. The products and services in BP[B] also need to be able to adapt to fast-paced market shifts and customer demands. For this reason, certain ways of working, methodologies, and processes need to be applied to how the development of the products and services are conducted (read agile, DevSecOps, Lean).

If execution is timely conducted and the market is penetrated within shortly identified time frames through well-timed marketing campaigns etcetera, the opportunities are high for generating large bottom-line profits for the organization. In the short term, Organization XYZ has accepted to take a high risk due to the high rewards from the potential opportunities.
Organization XYZ has chosen to emulate a start-up mentality through all the aspects within BP[B]. This implies employee skillset/competence, attitude, working methodologies, culture, mindset, technology, and so forth…and all these factors, as you may understand, have a carry-over to the Risk Tolerance, Capacity, and Appetite. This is true from both a holistic perspective for the organization and also from a business-oriented perspective.
The typical customers for BP[B] are early adopters and high-end customers seeking to be at the front end of the market curve.
Business Process C
BP[C] has today operated for 10 years. It is still considered young compared to BP[A] but matured in compression to BP[B].
At a starting point, 10 years back in time, when the development of the products in this business process started out a high-risk appetite and risk tolerance were taken in relation to BP[A] and BP[C].
Now BP[C] is operating in a steady environment, where risk-taking is still encouraged but due to dependencies on BP[A] the Risk Appetite and Risk Tolerance have been scaled down.

The experience Organization XYZ gained from BP[A] was used when building up the capabilities and fundamentals in BP[C]. The data, information, knowledge, and wisdom gained over a 10-year period, and those 100 years as an enterprise, were deeply contemplated when the business case for BP[C] was crafted.
The products in BP[C] are “hybrids”, they are built on mechanical components that are blended together and digitally transformed in a tempo with the market. In this Business Process, the goal is not to be the number on the market, as in BP[B].
The goal here is to penetrate a market and reach a customer seeking a transitional product before an eventual investment is made in the products or services provided by BP[B].
AGGREGATED VIEW
To summarize the description of the above information I have, with the help of the first model, illustrated this in the below figure.

ORGANIZATIONAL PERSPECTIVE
The overall Risk Capacity, Risk Tolerance, and Risk Appetite for Organization XYZ, viewed from a macro perspective, is illustrated below where each business process is aggregated into a single view.
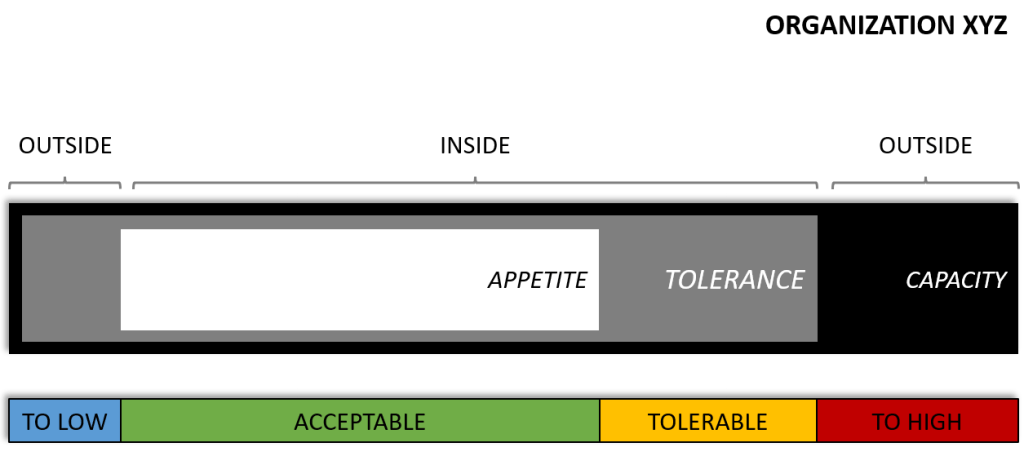
The overall risk mitigation strategy from a holistic organizational macro perspective for Organization XYZ has been to “isolate” Business Processes with a low Risk Tolerance and Appetite, such as BP[A]. The reason for this is to protect the organization from high negative impacting risks that may generate significant damage to the organization. This can for example be monetary, reputational, commercial, operational, or financial.
Organization XYZ is very risk-aware and calculating when it comes to risk/reward scenarios. This is for example clearly observed in the investments made in BP[B]. The risks are not only separated to gain effects of potential opportunities but also to preserve the monetary and reputational effects derived from the other business processes.
With the help of this methodology, Organization XYZ has also learned to use the knowledge and wisdom gained from previously made investments and developments in other business processes. Organization XYZ has also understood that the high risks taken in BP[B], where a significant digital footprint and utilization of software is conducted, also result in other kinds of threats and potential vulnerabilities.
This for example directly translates to adversarial external threat actors who have the skills and motivation to cause hard damage to Organization XYZ. The risks related to these forms of threats are drastically higher in BP[B]. If these threat actors exploit a potential vulnerability within BP[B] the damage will have a large negative financial impact on Organization XYZ.
However, the damage will be isolated organizationally and not propagated to other Business Processes. As mentioned before, the environment in BP[B] is totally separated from the rest of the organization. Organization XYZ has also made additional monetary investments in defensive cyber security capabilities (around Humans, Processes, and Technologies) within BP[B] to increase their resilience against modern cyber security threats and attacks. Organization XYZ realized they needed to keep up with the external threat and attack landscape.
Risk is based on the context in which it lives. Risk will change form and figure when the context shifts. The above scenario is one way how risk will change. A change in form and figure of risk will have dependencies on the threats, vulnerabilities, and assets that exist in the context. For this reason, I personally believe that a single top-level risk appetite statement, set at the board and executive leadership level, will work less good in reality. Risk appetite will vary within an organization and between different forms of risks (credit, brand, operational, market, sales, finance, security, safety).
If you want to know more about what a security risk is, check this article What is risk? Modeled & Explained.
EPILOGUE
Independent of how a theoretical concept, such as in this case Risk Appetite, Tolerance, and Capacity, is modeled I think that the expression and communication of it need to make sense for the audience. A complex model will in most cases make sense to an audience where there is a high degree of maturity around the subject. In certain cases, these audiences do not need any fancy models as they are already contemplating the subject with a very high level of expertise.
The things you have seen in this article about Risk Appetite, Tolerance, and Capacity are not a silver bullet solution. It will not make all mysteries go away but this is my attempt to reduce question marks and provide clarity around the subject.
Keep in mind that Risk Appetite, Tolerance, and Capacity are something within an organization that will shift in level/amount. And this is how it should be! The reflection of how the risk level/amount is carried out needs to be expressed and made applicable to the actual work, carried out in your organization, to help and guide your employees. A fluffy high-level risk appetite statement is not enough.

“We have a low risk appetite for cybersecurity risks […]” which may be a part of a risk appetite statement formulated at the executive level need to be translated to for example “…critical security updates shall be applied immediately to our internet-facing systems.” within the part of the organization who is responsible for the making sure to keep these systems protected. I think you get the drill. And I think this is one way how the theoretical concepts Risk Appetite, Tolerance, and Capacity can be made more understandable and transferable to the real world. Now those KRI’s (Key Risk Indicators) can be developed and assigned to monitor the risk level.
However, the work to do the translation and KRI development will not be done by itself. It is up to you, as a security leader to guide your organization and your stakeholders on the journey. You are there to support them to make that high-level statement understandable as a part of their day-to-day role and tasks. This is where the actual magic will take place. Risk is something that everyone in an organization is responsible for. Everyone needs to pitch in. Security is a team sport.
You have now reached the end of this article. Contemplate the information and try to see if you can put some of it into relation to your own organization through a thought experiment. Or maybe through visualizing your thoughts on a whiteboard or in PowerPoint?
Henrik Parkkinen